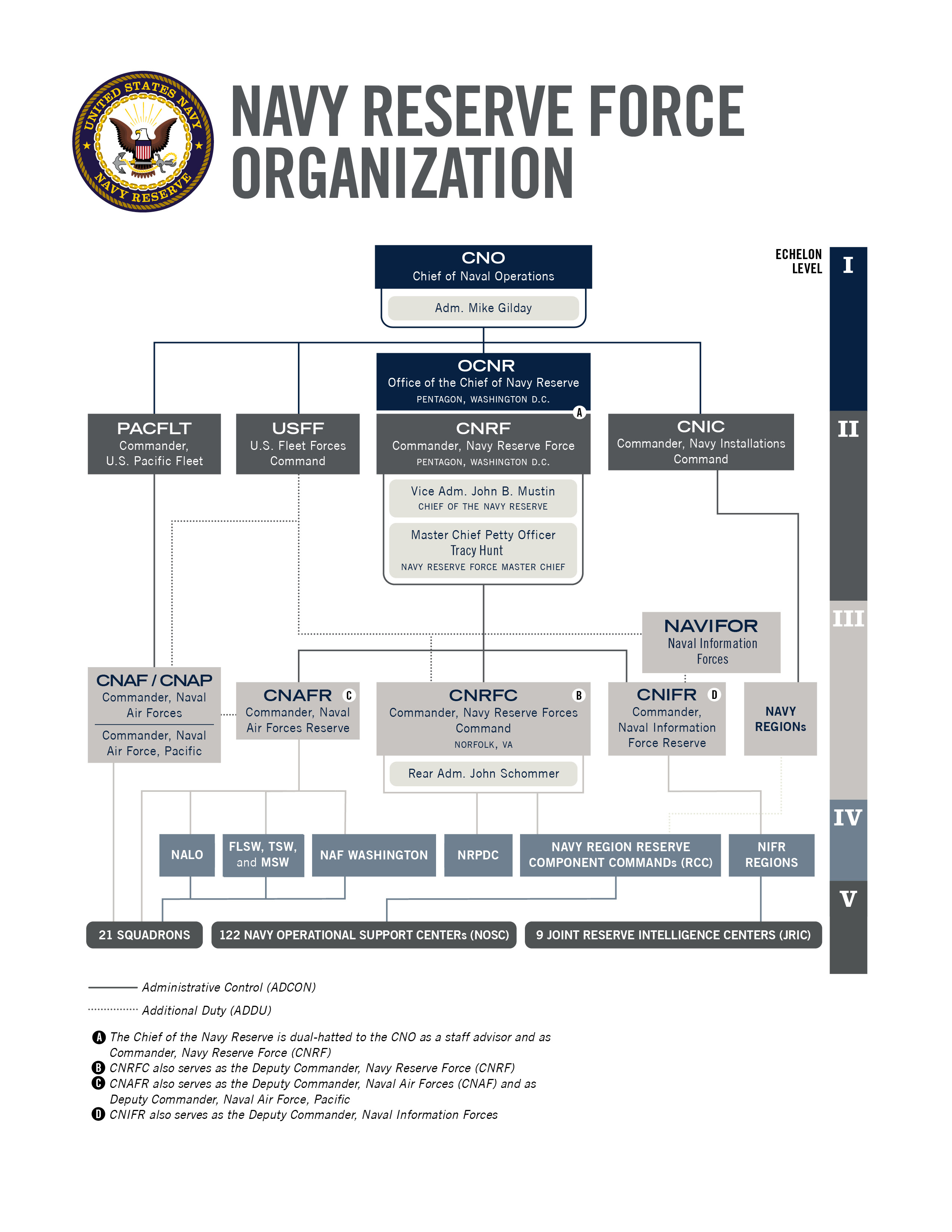
which of the following are breach prevention best practices jko
Access only the minimum amount of PHIpersonally identifiable information PII necessary Logoff or. Data loss protection DLP to detect and prevent data breaches by blocking the extraction of sensitive information.
Dod Cyber Awareness Challenge 2020 Your Ultimate Guide Infosec Insights
Data encryption solutions to render data inaccessible and unusable in.

. A breach as defined by the DoD is broader than a HIPAA breach. Create Strong Policies Strong Passwords. Developing the IRP will help the IT staff of the company to control the data breach incidents.
All of the above. Use strong passwords for every. 2 Which of the following are breach prevention best practices.
Identify areas that store transmit collect or process. Employees have an important role in keeping their organizations secure. Identity sensitive data collected stored transmitted or processes.
Which of the following are breach prevention best practices. Which of the following are breach prevention best practices. Select the best answer.
Invest in the Right. This includes ensuring that any new devices or software systems you bring on board are secure and updated with patches as needed. Implementing encryption standards and backup policies to decrease risks and make sure that.
30 Best Practices for Preventing a Data Breach. Which of the following are breach prevention best practices. At all levels should implement.
Making weak passwords can be a reason for Data. Which of the following are breach prevention best practices. D All Of The Above.
Best Practices for Preventing a Data BreachTrain Employees on Security Awareness.

Hipaa And Privacy Act Training Health Mil

Hipaa Pdf Dha Education And Training 1 15 2q 21 1 Under Hipaa A Covered Entity Ce Is Defined As 0 A Health Plan 0 A Health Care Course Hero

A Covered Entity Ce Must Have An Established Complaint Process False True Course Hero

Pdf Covid 19 Pandemic Geospatial Information And Community Resilience Greg Foliente Academia Edu

Which Of The Following Are Breach Prevention Best Practices All Of The Above You Course Hero

Hipaa And Privacy Act Challenge Exam Docx Hipaa And Privacy Act Training Challenge Exam Joint Knowledge Online Jko Dha Us001 Select Your Current Course Hero
Hipaa Jko Remedial Flashcards Quizlet

Scientific Program Of 34th World Congress Of Endourology Swl Program Book And Abstracts Journal Of Endourology
Hipaa And Privacy Act Training 1 5 Hrs Jko Flashcards Quizlet

Which Of The Following Are Breach Prevention Best Practices All Of The Above You Course Hero

D Arcy Duquette Dvcjduquette Twitter

Hipaa And Privacy Act Training Pre Test Answers Pdf 1 In Which Of The Following Circumstances Must An Individual Be Given The Opportunity To Agree Course Hero
A Huge List Of Cryptocurrency Thefts By Rokkex Hackernoon Com Medium

Which Of The Following Are Breach Prevention Best Practices Public Health

The Bar Review By Th Nk Media Issuu

Which Of The Following Are Breach Prevention Best Practices All Of The Above You Course Hero
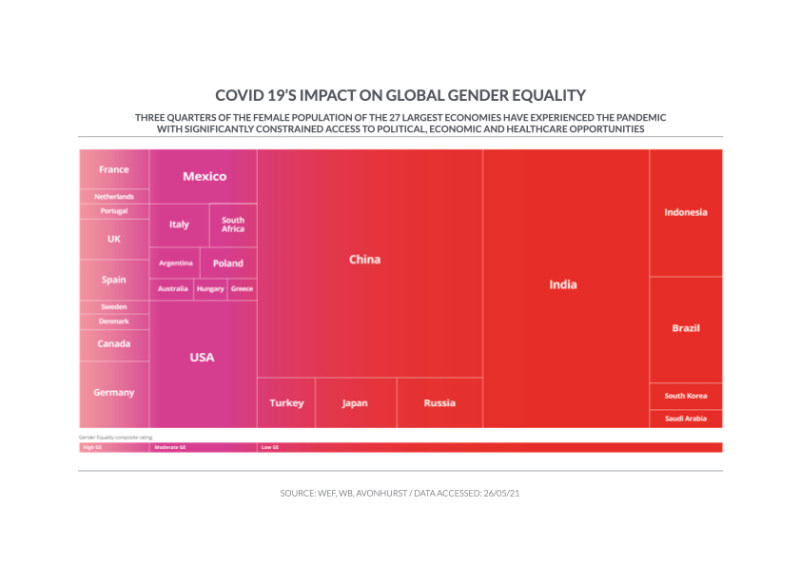
Good%20Year%20graphic.jpg?ver=aw99W3KoI9CzYK-tSAvkkw%3D%3D)